Connecting the application via SAML#
Connection data#
To connect an application to Blitz Identity Provider, you will need the data obtained during its registration:
the identifier assigned to the application in Blitz Identity Provider (
entityID);the metadata file of the service provider.
The application interacts with Blitz Identity Provider services using the following addresses:
Blitz Identity Provider metadata:
https://login-test.company.com/blitz/saml/profile/Metadata/SAML(test environment)https://login.company.com/blitz/saml/profile/Metadata/SAML(production environment)
URL for authentication:
https://login-test.company.com/blitz/saml/profile/SAML2/Redirect/SSO(test environment)https://login.company.com/blitz/saml/profile/SAML2/Redirect/SSO(production environment)
URL for the logout:
https://login-test.company.com/blitz/saml/profile/SAML2/Redirect/SLO(test environment)https://login.company.com/blitz/saml/profile/SAML2/Redirect/SLO(production environment)
Publisher’s URL:
https://login-test.company.com/blitz/saml/(test environment)https://login.company.com/blitz/saml/(production environment)
If the application supports the SAML connection protocol, then the specified data should be sufficient to configure the application. If the application does not support the SAML protocol, it should be modified according to the recommendations set out in the sections: Ready-made libraries and Principle of integration.
Typical questions about how to set up an application to connect to Blitz Identity Provider over the SAML protocol:
Where can I find the metadata of the identity provider?
To download the metadata, follow the link https://login.company.com/blitz/saml/profile/Metadata/SAML and copy the open XML document into the application.
Where can I find the SAML certificate of the identity provider?
Open the XML document with the metadata of the identity provider. Find the section <ds:X509Certificate></ds:X509Certificate> – this is where the SAML certificate of the identification provider is located. Example:
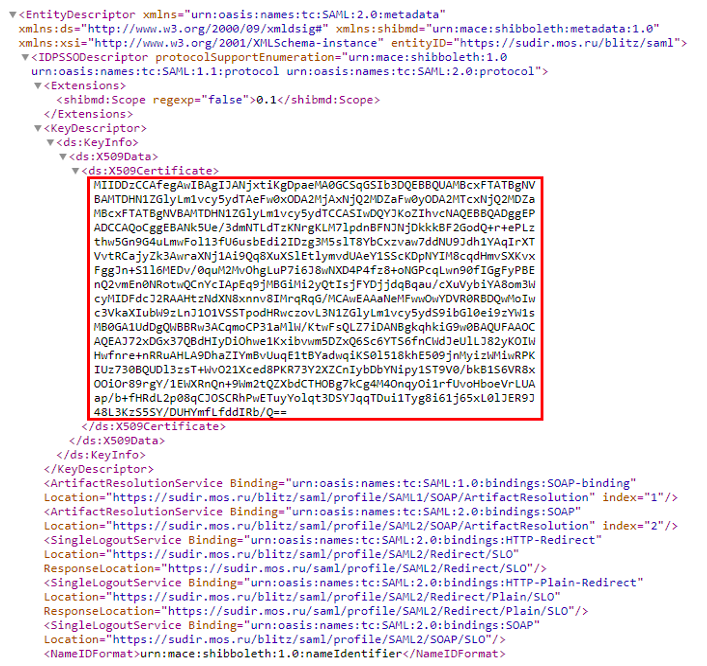
Sometimes, in order to load correctly into the application, you need to insert the line -----BEGIN CERTIFICATE----- before the line with the certificate, and after – -----END CERTIFICATE-----
Where can I find the addresses of the SAML handlers of the identity provider?
The application should send identification/authentication requests to the following handlers (SingleSignOnService) in the PROD‑environment:
https://login.company.com/blitz/saml/profile/SAML2/Redirect/SSO– a standard SAML handler is used to receive requests compressed using the Deflate algorithm.https://login.compan y.com/blitz/saml/profile/SAML2/Redirect/Plain/SSO– for receiving uncompressed requests – should be used only if the connected application does not usedeflate.
The application should send requests for a single logout to the following handlers (SingleLogoutService) in the PROD‑environment:
https://login.company.com/blitz/saml/profile/SAML2/Redirect/SLO– a standard SAML handler is used to receive requests compressed using the Deflate algorithm.https://login.compan y.com/blitz/saml/profile/SAML2/Redirect/Plain/SLO– for receiving uncompressed requests – should be used only if the connected application does not usedeflate.
In the TEST environment, similar addresses start with https://login-test.company.com.
What is the entity ID of the identity provider?
Blitz Identity Provider as an identification provider, it has the following entityID:
For the PROD-environment –
https://login.company.com/blitz/samlFor the TEST-environment –
https://login-test.company.com/blitz/saml
Ready-made libraries#
Since self-development of the SAML client software interface is a time-consuming task, and implementation errors are fraught with security threats, it is recommended to use existing popular SAML client libraries when integrating an application using SAML:
OIOSAML (Java, .NET),
OpenSAML (Java),
Spring Security SAML (Java),
SimpleSAMLphp (PHP),
ruby-saml (Ruby on Rails).
The following are the key information needed to understand the SAML authentication process.
Principle of integration#
To connect to Blitz Identity Provider in order to identify and authenticate users, the application can use the SAML standard versions 1.0, 1.1, 2.0.
In this case, the process of interaction between the application and Blitz Identity Provider should be built in accordance with the profile SAML Web Browser SSO Profile.
The SAML standard is based on XML and defines ways to exchange information about user authentication and their identification data (attributes, permissions).
In order to be able to interact, the service provider and the identity provider must first exchange interaction settings described in the form of XML documents and called metadata. The service provider should receive the Blitz Identity Provider settings called identity provider metadata.
Identification and authentication#
See the description of the interaction between a web app and Blitz Identity Provider via SAML.
Logout#
An application connected to Blitz Identity Provider by SAML may also provide for the possibility of implementing a single logout. For these purposes Blitz Identity Provider supports SAML Single Logout Profile. The application can send a <LogoutRequest> SAML-request to Blitz Identity Provider and, if the single logout is completed successfully, receive a <LogoutResponse> SAML-response from Blitz Identity Provider. If the application should be involved in a single logout initiated by another application connected to Blitz Identity Provider, then it should also provide the ability to process <LogoutRequest> requests received by the application from Blitz Identity Provider. In case of successful completion of the local session, the application should notify Blitz Identity Provider by sending it a SAML response <LogoutResponse>.