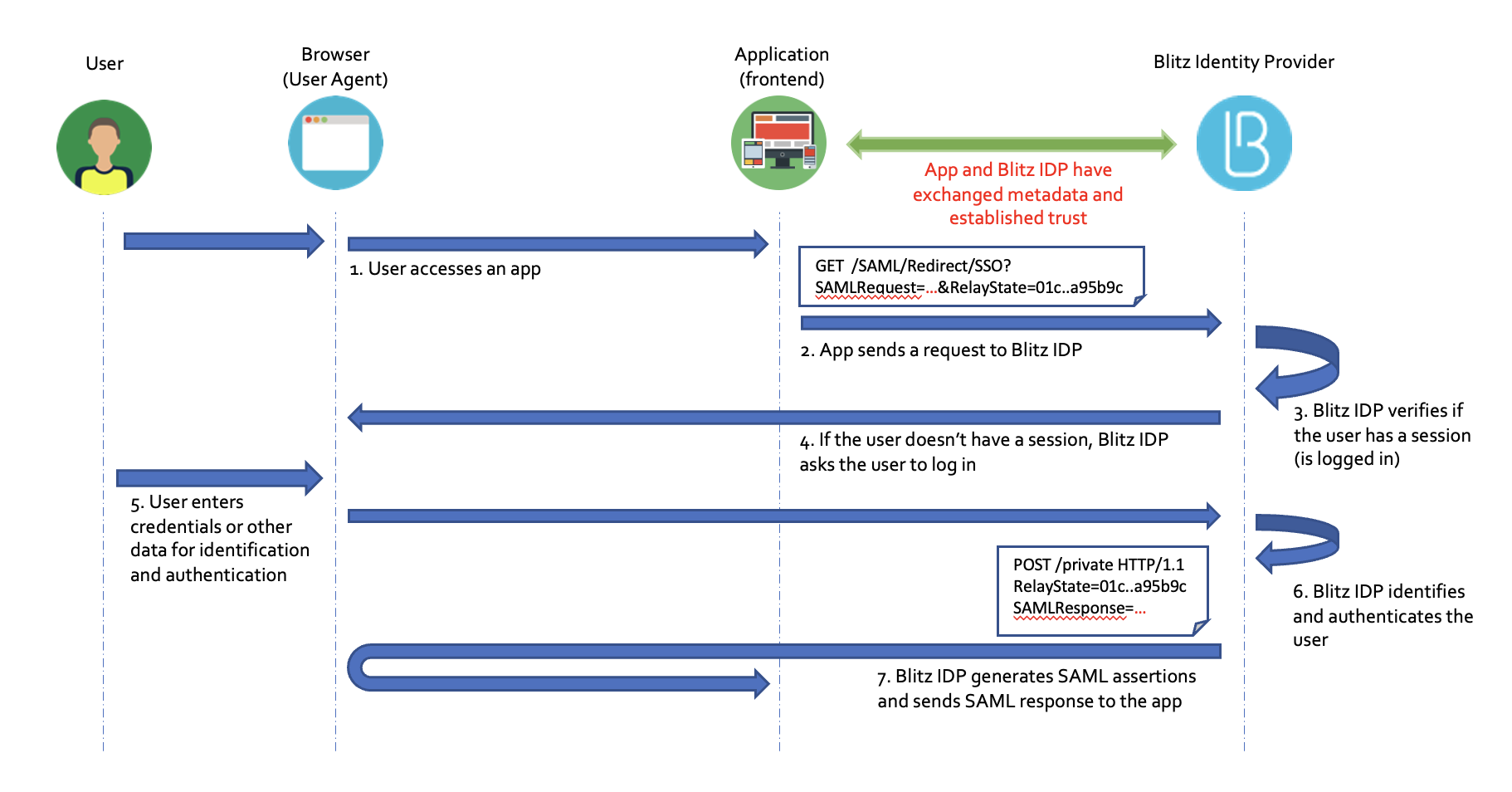
Connecting an app via SAML#
During the interaction, the application (service provider) sends a SAML request to Blitz Identity Provider for user identification (SAML Request). The request is an XML document designed in accordance with the SAML standard. The request contains the identifier of the application requesting identification, called the entityID, as well as additional service information. The request itself is transmitted electronically signed by the application. The HTTPS protocol is used as the transport protocol for transmitting a message, and the identification provider is called via HTTP Redirect. This means that the request from the application to Blitz Identity Provider is made indirectly, through the user’s browser, and direct network interaction between the application and Blitz Identity Provider is not required when using SAML.
After receiving a SAML identification request, Blitz Identity Provider identifies the request belonging to a specific application, after which it displays a single sign-on web page to the user to identify and authenticate the user. In case of successful identification and authentication of the user, Blitz Identity Provider transmits a SAML Response to the application (service provider). Depending on the set interaction settings, the request can be signed and encrypted. XML Signature and XML Encryption standards are used for signature generation and encryption. The HTTPS protocol is used as a transport protocol for transmitting a message with identification results, and the service provider is called via HTTP POST.
After receiving a SAML response from Blitz Identity Provider, the application verifies its signature, performs decryption, and then extracts user identification data (identifiers, attributes, permissions) from SAML statements.
The process of interaction between the application and Blitz Identity Provider using SAML is shown in the figure.
User identification using SAML