About Blitz Keeper#
With the Blitz Identity Provider, you can implement access control when secured services are invoked by applications.
Providing authorization when applications invoke services is based on OAuth 2.0 specifications. Before using services, an application must obtain an access token (access_token) from Blitz Identity Provider. Various interaction methods are available to the application to obtain an access token. The access token can be obtained:
in the context of a user login - the token will include information about the user and a set of scopes (permissions) granted by the user to the application;
to the application outside of the user login - the token will include a set of scopes (permissions) from the granted to the application.
Then using the access token obtained, the application can invoke services. In doing so, the following complications will occur:
within each service it will be necessary to implement its own authorization logic – check the provided access token, extract information about the user and provided consents (permissions) from them, and analyze whether those permissions are sufficient for service to be executed.
the application will use a single access token to invoke different services. In this case, the access token may contain more information about the user and a larger set of consents (permissions) than is necessary for a particular invoked service. This will violate the principle of least privilege - the service will get more access rights than it needs to perform its task.
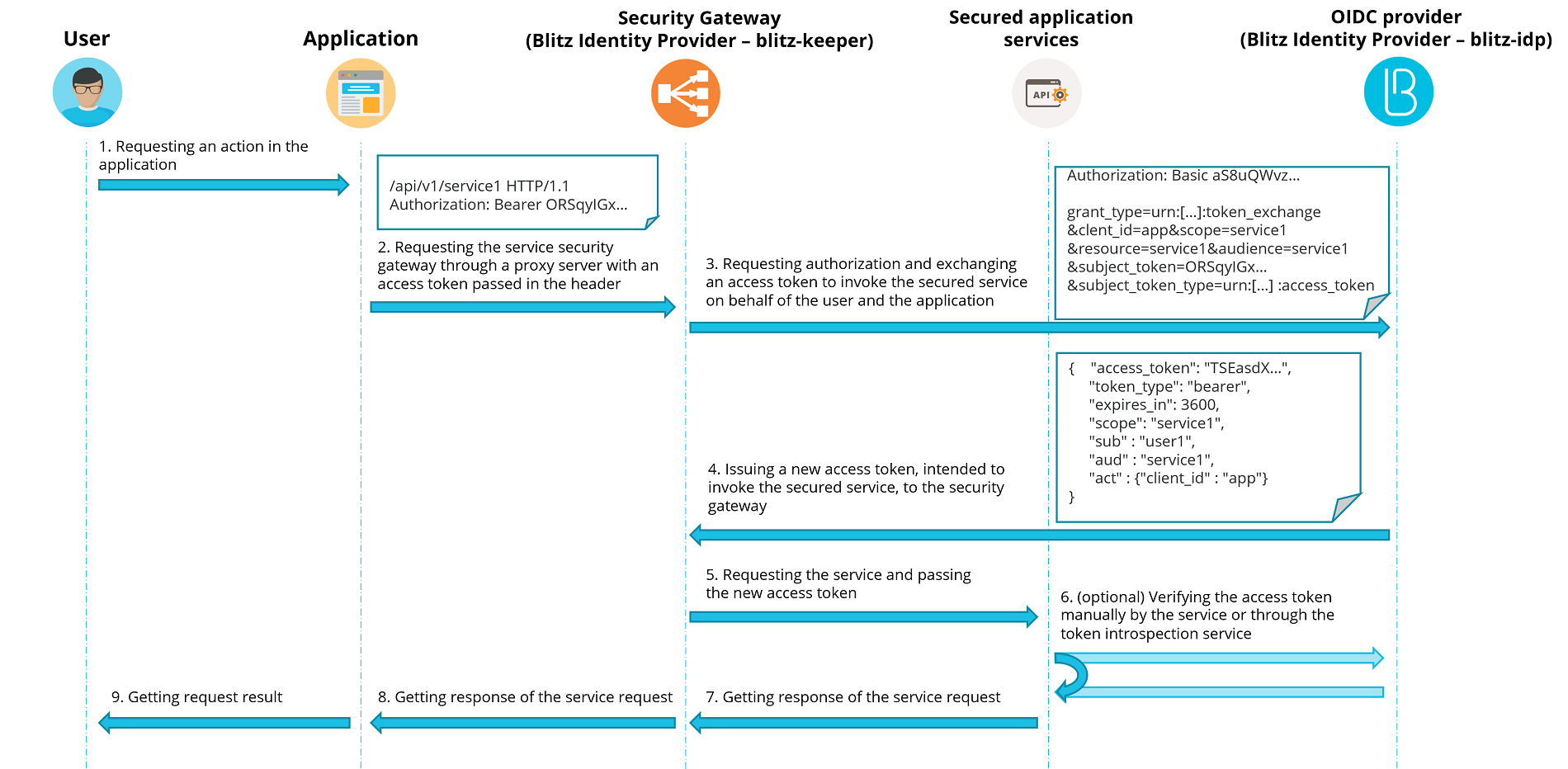
To solve the above described difficulties, Blitz Identity Provider provides a special application - the Security Gateway (blitz-keeper). This application is a specialized proxy server used when calling protected services - the application does not call the services directly, but through the Security Gateway. The Security Gateway takes care of the following tasks:
Checks the authorization header included in the invoke of service, extracts the access token and, in interaction with the authorization service (
blitz-idp), checks whether the access token is valid, and whether the user and the application has sufficient access rights to invoke the secured service.In interaction with the authorization service (
blitz-idp) replaces the access token in such a way that the security token transmitted from the Security Gateway to the protected service contains only the set of user information and permissions required for the protected service operation. Redundant permission and user information can be either removed from the security token or additional permissions and information added to the access token, if this is configured in the security policy.Logs successful and unsuccessful access control events in the Blitz Identity Provider security event log.
The interaction between the Security Gateway and the authorization service is based on the OAuth 2.0 Token Exchange specification. Picture of the interaction is shown in the diagram.
Configuring the use of the security gateway to access protected services is described in the following sections.