Blitz Panel configuration#
To configure Blitz Panel, do the following:
Put application icons into the
/usr/share/identityblitz/blitz-panel/static/resources/icons/directory.Note
The following formats are supported:
SVG,
PNG, maximum 128px on the minimum side.
In Blitz Identity Provider, create an application to connect Blitz Panel to Blitz Identity Provider via OAuth 2.0.
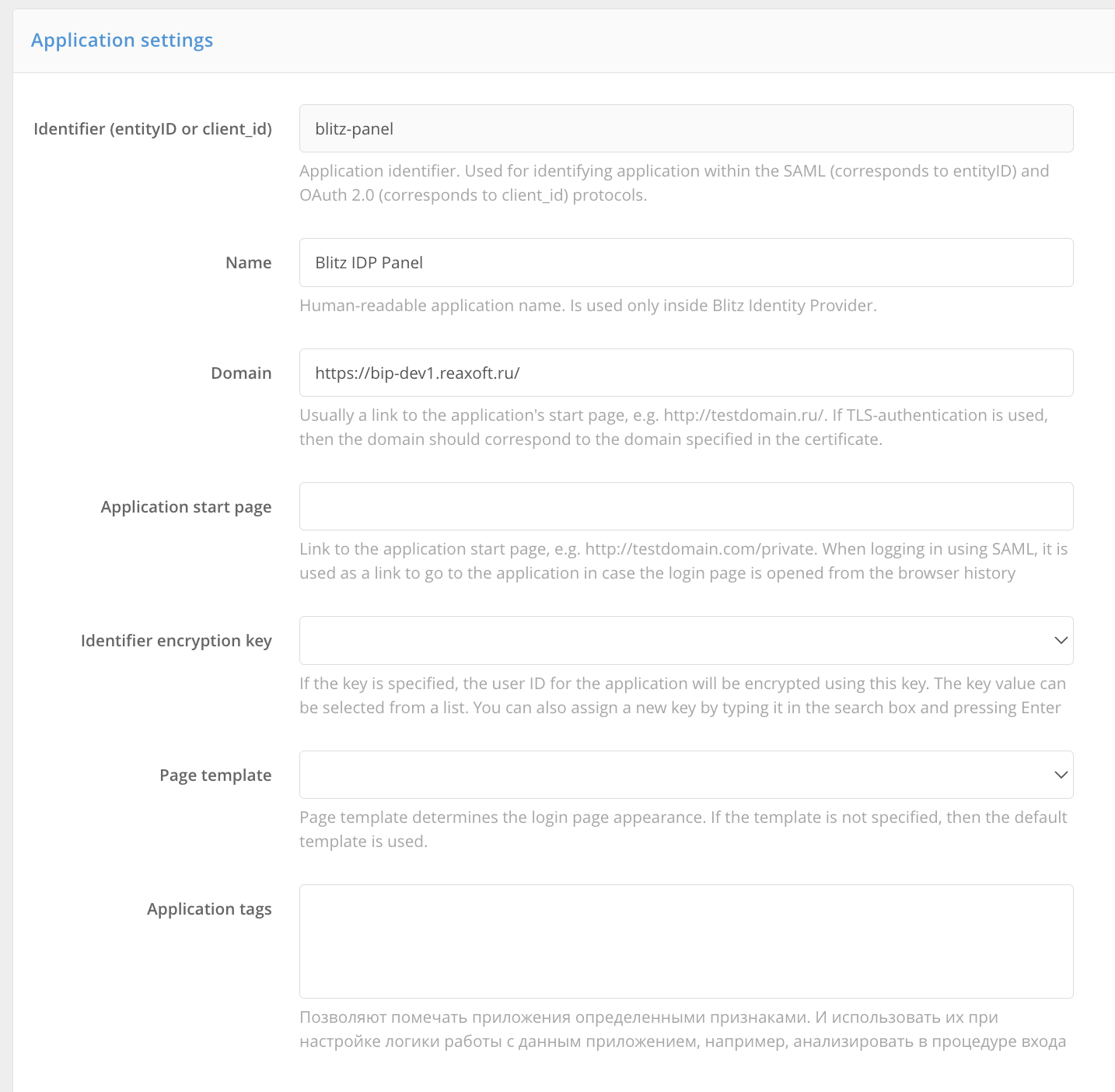
Specify
client_idandclient_secretset during the Blitz Panel installation.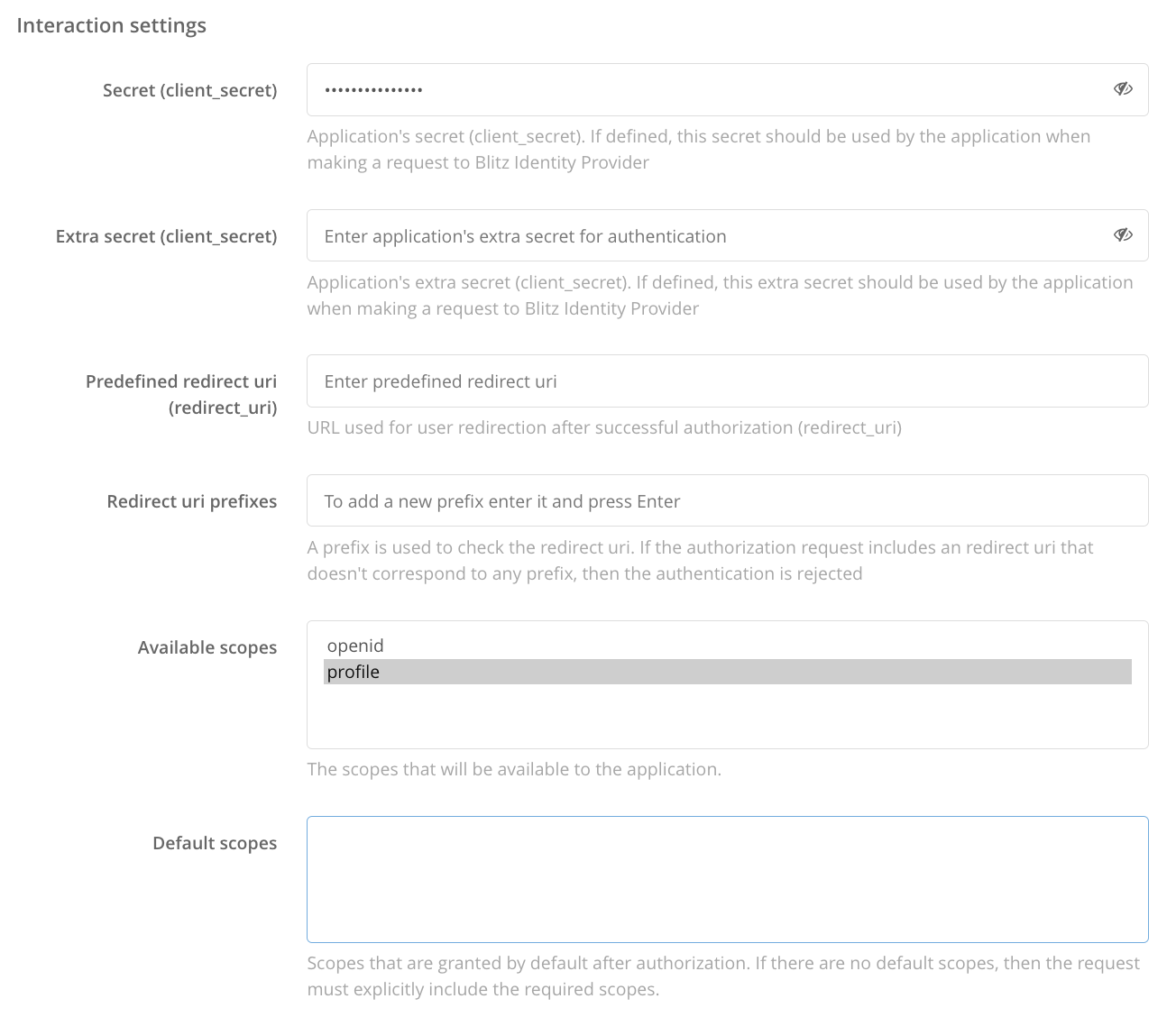
Be aware that you need to copy the URLs of API requests from the Protocols section to the
/etc/blitz-panel/app.confconfiguration file (see the next step).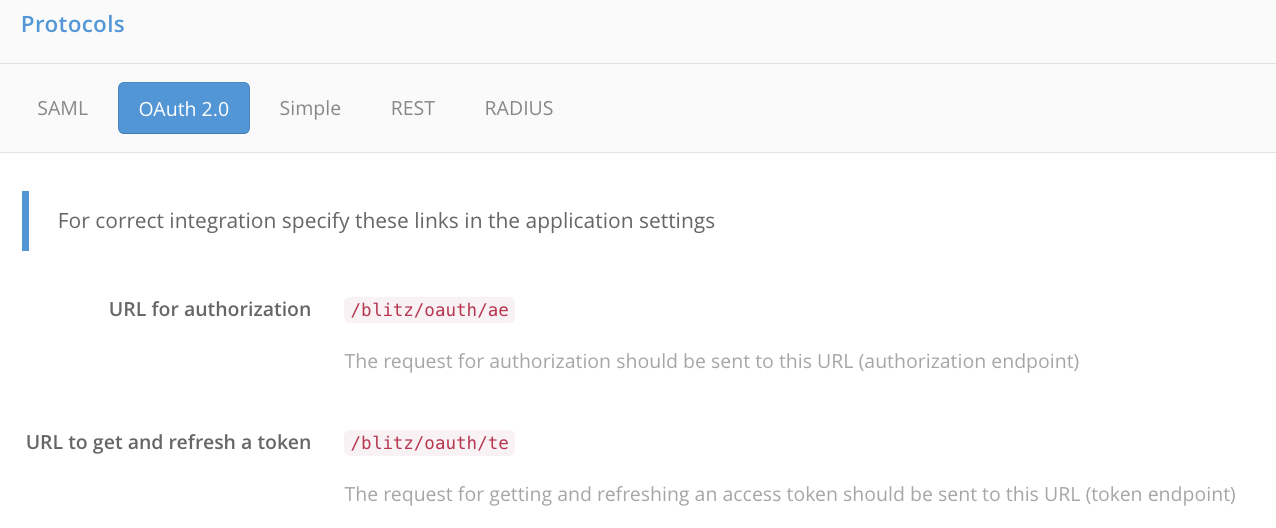
Tip
The values of
client_idandclient_secretset during the Blitz Panel installation can be changed if necessary in the same configuration file.Open the
/etc/blitz-panel/app.confconfiguration file. In thesession->oauthsection, set parameters to connect the Blitz Panel application to Blitz Identity Provider via OAuth 2.0.name: arbitrary connection name;clientId: check if theclient_idapplication identifier matches the one specified in Blitz Identity Provider.clientSecret: check if the application secret key matches the one specified in Blitz Identity Provider.logoutUrl: URL that will be used by Blitz Panel to send the logout request to Blitz Identity Provider.authUrl: URL that will be used by Blitz Panel to send the user authorization request to Blitz Identity Provider.tokenUrl: URL that will be used by Blitz Panel to send the request to Blitz Identity Provider to obtain or update an access token.me: URL (url) that will be used by Blitz Panel to send the request to Blitz Identity Provider to receive a user data, and an attribute (subjectIdAttr) to search for a user in the storage.scopes: list of permissions that will be available to Blitz Panel.
"session": { "oauth": { "name": "Blitz IdP", "clientId": "CHANGE_CLIENT_ID", "clientSecret": "CHANGE_CLIENT_SECRET", "logoutUrl": "https://CHANGE_IDP_DOMAIN/blitz/login/logout", "authUrl": "https://CHANGE_IDP_DOMAIN/blitz/oauth/ae", "tokenUrl": "https://CHANGE_IDP_DOMAIN/blitz/oauth/te", "me": { "url": "https://CHANGE_IDP_DOMAIN/blitz/oauth/me", "subjectIdAttr": "sub" }, "scopes": [ "openid", "profile" ] }, ... }, ...
If necessary, set a user session parameters: the URL to which the user will be redirected after logging out, the TTL value, the maximum period of inactivity in seconds, the period between the session activity checks in milliseconds, the created
cookiename, etc."session": { ... "postLogoutUrl": "/blitz/panel", "ttlInSec": 36000, "inactivityPeriodInSec": 3600, "checkSessionPeriodInMs": 1000, "cookie": { "name": "scs", "path": "/blitz/panel", "transient": true }, "useCompression": false, "encodingKey": "CHANGE_SCS_ENC", "hmacKey": "CHANGE_SCS_HMAC" }, ...
The
apps->sourcessection contains groups of applications that can be formed according to arbitrary characteristics (static, dynamic, etc.). Each group has a name, a list of applications in the group, and rules that determine which users the applications are shown to.In the
apps->sources->rulessection, set the rules that determine for which users certain applications will be displayed.Each rule consists of the following parts:
name: the rule name.conditions: conditions for user selection.The following types of conditions are supported:
"typ": "userGroup"- user group. You must specify the group profile name and group ID."typ": "userClaims"- flexible selection of users based on the claims regarding their attributes. A condition of this type can contain statements on multiple attributes. In order for a user to be selected according to a condition, they must satisfy all statements in it.
Attention
A rule can contain multiple conditions. A rule is applied to a user if the user meets at least one condition.
tags: tags linking user selection rules and applications.The following types of tags are supported:
arbitrary parameter (for example,
role,department, etc.);application identifier (set in the
appIdlist).
Attention
A rule is applied to an application if at least one of the values specified in this section is present in the application settings (see the next step).
In the
apps->sources->appssection, set the list of applications connected to Blitz Identity Provider, that will be displayed on the panel. For each application, specify the following settings:id: application ID in Blitz Identity Provider.name: the name of the application that will be displayed on the panel, in required languages.url: URL of the application’s start page.icon: icon file name in the directory:/usr/share/identityblitz/blitz-panel/static/resources/icons/``
tags: tags that determine for which users the application will be displayed on the panel according to the rules specified above (optional).desc: description of the application in required languages.
Example of setting up rules and application list#"apps": { "sources": [ { "name": "Static Applications", "type": "static", "apps": [ { "id": "dev_portal", "name": { "en": "Developer Tools 24" }, "url": "https://my.domain.com/dev/portal", "icon": "confluence.svg", "tags": { "role": [ "admin", "sys_admin" ] } }, { "id": "jira", "url": "https://my.domain.com/dev/jira", "name": { "ru": "Jira" }, "icon": "jira.svg", "tags": { "role": [ "admin", "sys_admin" ] } }, { "id": "test-app", "url": "https://my.domain.com/dev/test", "name": { "en": "Test application" } }, { "id": "atom", "url": "https://my.domain.com/dev/atom", "name": { "en": "Atom" }, "desc": { "en": "Atom is your essential companion" } }, { "id": "call_center", "url": "https://my.domain.com/dev/call", "name": { "en": "Call center" }, "desc": { "en": "Call center management application" }, "tags": { "role": [ "admin", "sys_admin" ] } }, { "id": "web_mail", "name": { "en": "Mailbox" }, "desc": { "en": "Corporate mailbox" }, "icon": "gmail.svg", "url": "https://my.domain.com/dev/portal", "tags": { "role": [ "sys_admin" ] } }, { "id": "yandex", "url": "https://my.domain.com/dev/yandex", "name": { "en": "Search engine" }, "desc": { "en": "Search engine web interface" } } ], "rules": [ { "name": "admin_role", "conditions": [ { "typ": "userGroup", "profile": "main_group_profile", "id": "app_admin" }, { "typ": "userClaims", "claims": { "company_type": "IT", "position": [ "head", "master" ] } }, { "typ": "userClaims", "claims": { "company_name": "Моя компания" } } ], "tags": { "appId": [ "dev_portal", "yandex" ], "role": [ "admin", "sys_admin" ] } }, { "name": "atom", "conditions": [ { "typ": "userClaims", "claims": { "tags": [ "atom" ] } } ], "tags": { "appId": [ "atom" ] } } ] } ] }, ...
Add the
blitz-panelservice to autostart and launch it:systemctl enable blitz-panel systemctl start blitz-panel