Preparing for Installation#
When deploying the Blitz Identity Provider, you need to setup and configure:
Web Server. You can use your company’s existing web server to load balance and remove SSL encryption from incoming traffic.
Blitz Identity Provider applications - Authentication Service, Enrollment Application, Access Recovery Application, Security Gateway, Admin Console. You do not need to install the Enrollment, Access Recovery, and Security Gateway applications if you do not plan to use their related features.
DBMS. You can use Couchbase Server, PostgreSQL, Postgres Pro, Jatoba.
Attention
Interaction of Blitz Identity Provider with PostgreSQL is performed via JDBC. Any relational DBMS with JDBC support can be used instead of PostgreSQL, but it should be separately agreed with REAK SOFT LLC within the framework of the corresponding implementation projects.
Account and password storage. You can use an LDAP server, Microsoft Active Directory, or any (you will need to develop a connector) existing system for storing accounts and passwords.
Queue server - RabbitMQ is used. It is also possible to configure the transmission of security reports to Kafka.
Deployment is possible in a low-resource configuration or in a cluster configuration.
Minimum deployment requirements#
Deployments with medium availability and performance requirements are recommended for preparation of test environments and production loops.
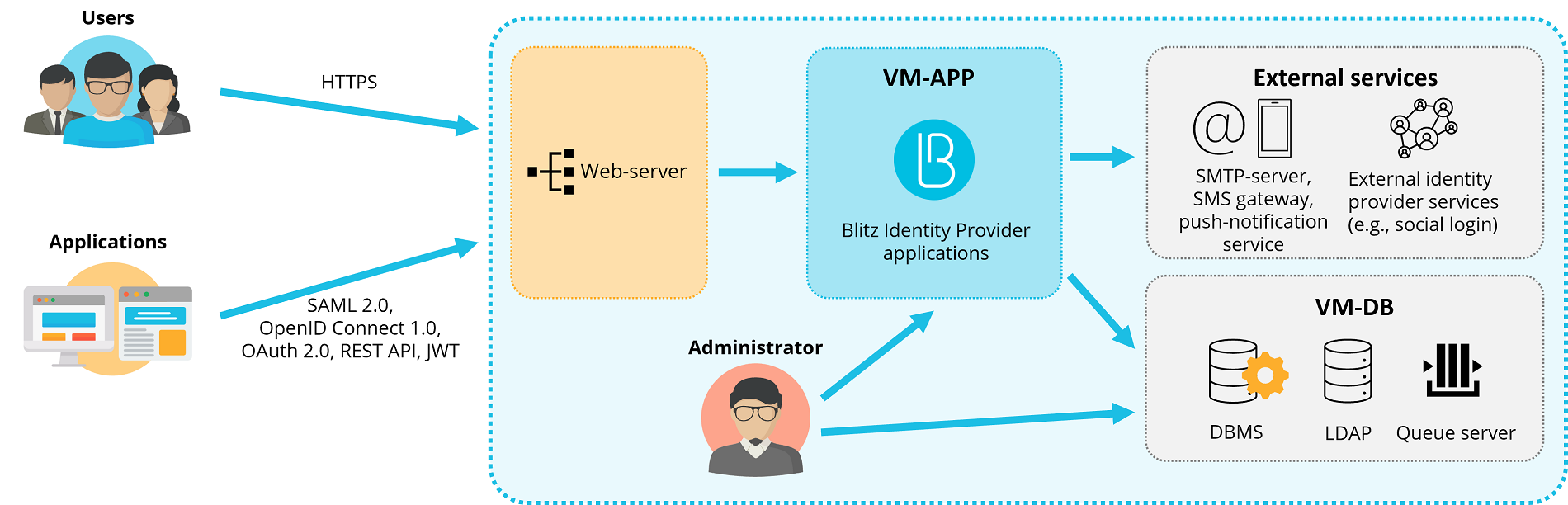
Deployment in minimal configuration
2 virtual machines (hereinafter - VMs) with the following characteristics and roles is a minimum requirement for the deployment.
Minimum sever requirements for deployment
Description |
OS |
Technical specifications |
Software |
|---|---|---|---|
VM for Applications (VM APP) |
|
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
|
Database VM (VM DB) |
|
4 CPU cores, 8 GB RAM, 100 GB HDD |
|
Required software versions:
OpenJDK 8, Liberica JDK 8, Axiom JDK 8 Certified or Oracle JDK 8;
Memcached memory manager version 1.4.15 or higher.
Network connectivity requirements:
VM-NLB shall be accessible via
80,443(HTTP/HTTPS) from user networks;VM-APP must have access:
to VM-DB via
8091,8092,8093,11209,11210,11211,4369,21100to21199,11214,11215,18091,18092(standard Couchbase Server ports),5432(standard PostgreSQL port),389,636(standard LDAP ports),5672(standard RabbitMQ port);to external identity provider services via
443port (if used):Type
Reference
Social networks
https://appleid.apple.comhttps://accounts.google.comhttps://graph.facebook.comto SMS gateway (if used);
to SMTP (if used);
to push notification service (if you use it);
to the Kafka service (when used to receive security reports).
For VM-APP, you need to create a public DNS name (for example, auth.domain.ru) and issue a TLS certificate for auth.domain.ru or *.domain.ru.
Recommended deployment requirements in a cluster#
Deployment in a cluster configuration is shown in the figure below. Recommended for use when building productive authentication loops with high availability and peak performance requirements.
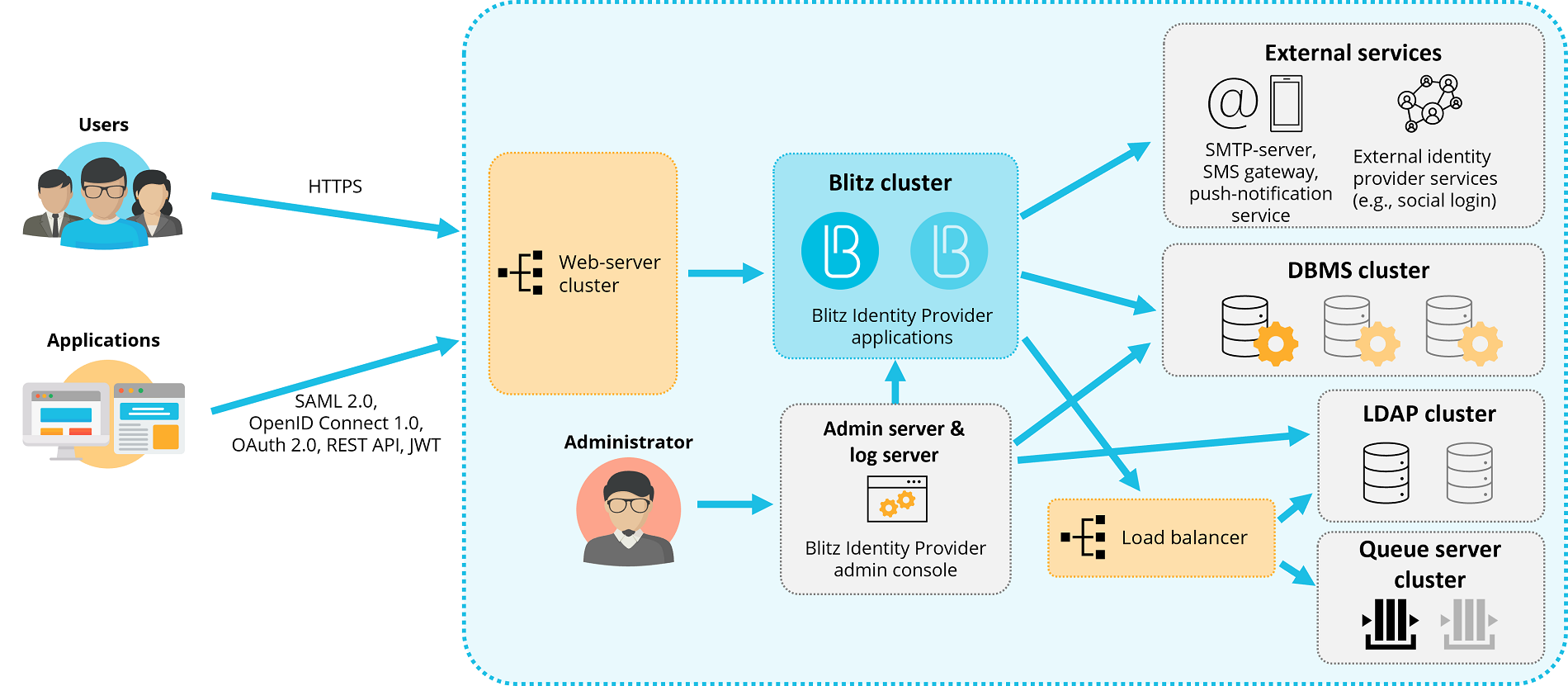
Deployment in a cluster configuration
For deployment in a cluster configuration, it is recommended to use Virtual Machines (VMs) with the characteristics and functions listed in the table below.
Recommended server requirements for deployment in a cluster
Description |
Q-ty |
OS |
Technical specifications |
Software |
Comment |
|---|---|---|---|---|---|
VM for web-servers (VM-WEB) |
1-2 |
|
4 CPU cores, 4 GB RAM, 50 GB HDD |
nginx |
You can use an existing web server to load balance and remove TLS from incoming traffic |
Blitz Identity Provider Application VM (VM-APP) |
2 |
|
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
|
It is recommended deploy each application of Blitz Identity Provider in on its own cluster on separate servers under heavy load |
VM for console (VM-ADM) |
1 |
|
2 CPU cores, 4 GB RAM, 100 GB HDD |
|
It is recommended to configure this server to collect logs from different servers in the Blitz Identity Provider cluster |
VM for DBMS (VM-DB): |
2-3 |
|
For PostgreSQL: 4 CPU cores, 8 GB RAM, 100 GB HDD (data), 50 GB HDD (system). For Couchbase Server: 8 CPU cores, 16 GB RAM, 500 GB HDD (data), 100 GB SSD (indexes), 50 GB HDD (system). |
PostgreSQL software (9.6 or later) or Couchbase Server Community Edition (6.0 or later) |
For PostgreSQL, it is recommended to allocate one physical server for the main instance and one for standby. For Couchbase Server it is recommended minimum 3 VMs. |
VM ofr LDAP (VM-LDAP) |
2 |
|
4 CPU cores, 8 GB RAM, 100 GB HDD |
389 Directory Server |
As a storage you can use an existing storage based on LDAP, Microsoft Active Directory, FreeIPA, or other system of storing accounts and passwords (connection via REST connector). |
VM for Queue server (VM-MQ) |
1-2 |
|
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
RabbitMQ version 3.7.9 |
Using a Queue server is optional |
VM for the Load balancer (VM-NLB) |
1-2 |
|
2 CPU cores, 4 GB RAM, 50 GB HDD |
HAProxy, keepalived |
Internal balancer is needed in case of LDAP and Queue server clustering |
Required software versions:
OpenJDK 8, Liberica JDK 8, Axiom JDK 8 Certified or Oracle JDK 8;
Memcached memory manager version 1.4.15 or higher;
Network connectivity requirements:
VM-NLB shall be accessible via
80,443(HTTP/HTTPS) from user networks;from VM-WEB there must be access to VM-APP via
9000(blitz-idp),9002(blitz-registration),9003(blitz-recovery),9012(blitz-keeper) and VM-ADM via9001(blitz-console);VM-APP must have access:
to other VM-APPs and VM-ADMs via
11211(memcached);to VM-DB via
8091,8092,8093,11209,11210,11211,4369,21100to21199,11214,11215,18091,18092(standard Couchbase Server ports) or5432(standard PostgreSQL port);to VM-LDAP (VM-NLB) via
389,636(standard LDAP ports);to VM-MQ (VM-NLB) via
5672(the standard RabbitMQ port);to external identity provider services via
443port (if used):Type
Reference
Social networks
https://appleid.apple.comhttps://accounts.google.comhttps://graph.facebook.comto the SMS gateway (if used);
to SMTP (if used);
to push notification service (if you use it);
to the Kafka service (when used to receive security reports).
VM-ADM must have access:
to VM-DB via
8091,8092,8093,11209,11210,11211,4369,21100to21199,11214,11215,18091,18092(standard Couchbase Server ports) or5432(standard PostgreSQL port);to VM-LDAP (VM_NLB) via
389,636(standard LDAP ports);to VM-APP via
22(ssh),514(rsyslog),11211(memcached);to VM-MQ (VM-NLB) via
5672(the standard RabbitMQ port);to the Kafka service (when using it to receive security reports)
from the VM-DB shall have access to other VM-DBs via
8091,8092,8093,11209,11210,11211,4369,21100-21199,11214,11215,18091,18092(Couchbase Server ports) or5432(PostgreSQL port);with VM-LDAP there must be access to other VM-LDAPs via
389,636(LDAP ports);from the VM-MQ must have access to other VM-MQs via
4369,35197,5672.
For VM-APP, you need to create a public DNS name (for example, auth.domain.ru) and issue a TLS certificate for auth.domain.ru or *.domain.ru.