Registering applications in Blitz Identity Provider#
About applications#
Application registration in Blitz Identity Provider is required so that applications can use the services provided by Blitz Identity Provider:
request user identification and authentication;
invoke the Blitz Identity Provider REST services.
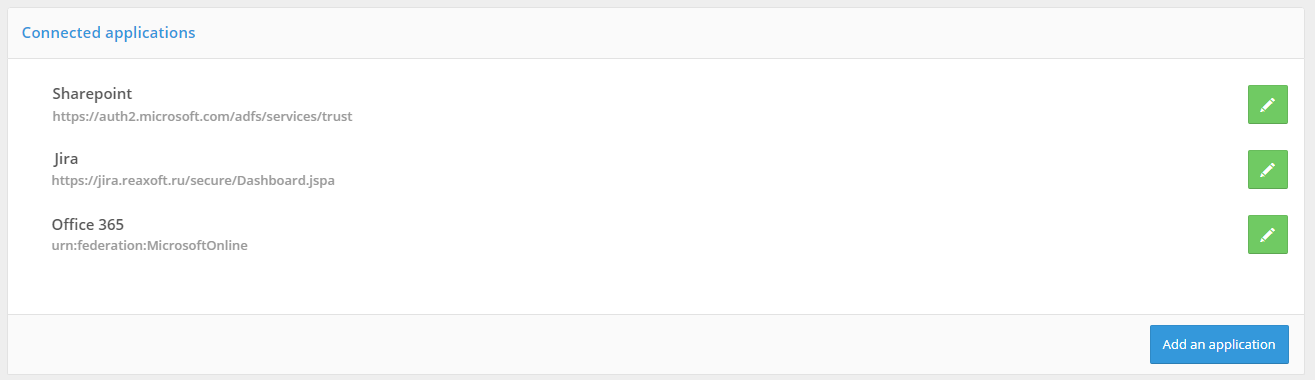
Applications are managed in the section Applications of the Admin Console.
Creating a new application account#
To connect a new web application, go to the Applications section of the console and select Add application. This action will launch the new application connection wizard, which includes the following steps:
Step 1. Basic settings
It is required to specify the identifier of the application to be connected (when connecting via SAML protocol, the identifier corresponds to entityID, when connecting via OAuth 2.0 - client_id), its name and domain, i.e. the URL where this application is available.
Important
When specifying the identifier for OAuth 2.0 it is not allowed to use colon and tilde.
The name of the application is then used by Blitz Identity Provider to display on the login page when the application initiates a request for user identification.
The application domain is used when a user needs to be redirected to the application from Blitz Identity Provider web pages. The redirection is done to the specified domain or to a specialized redirect_uri passed in the interaction with Blitz Identity Provider, but it is verified that redirect_uri corresponds to the domain specified in the application configuration.
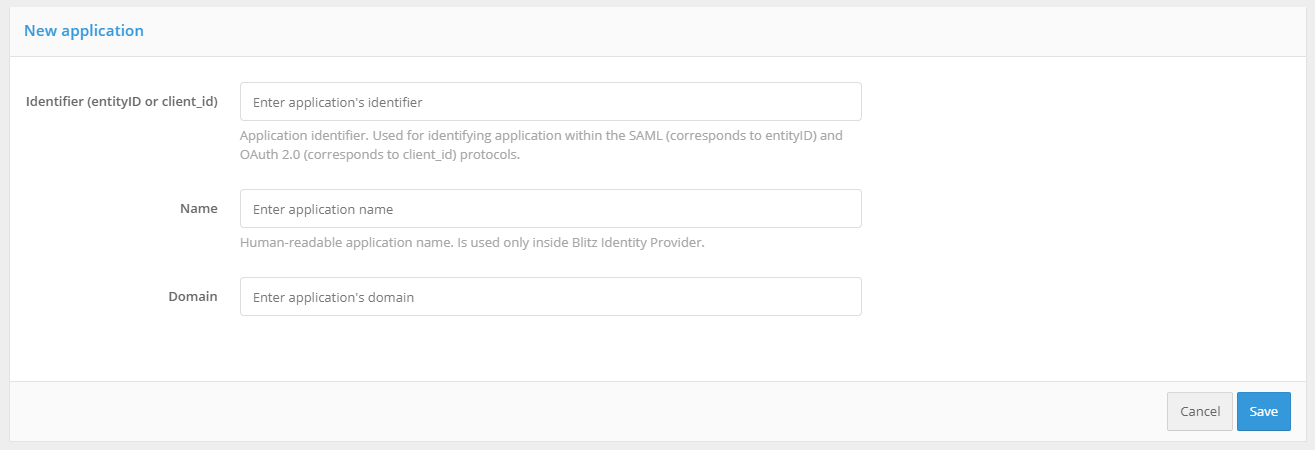
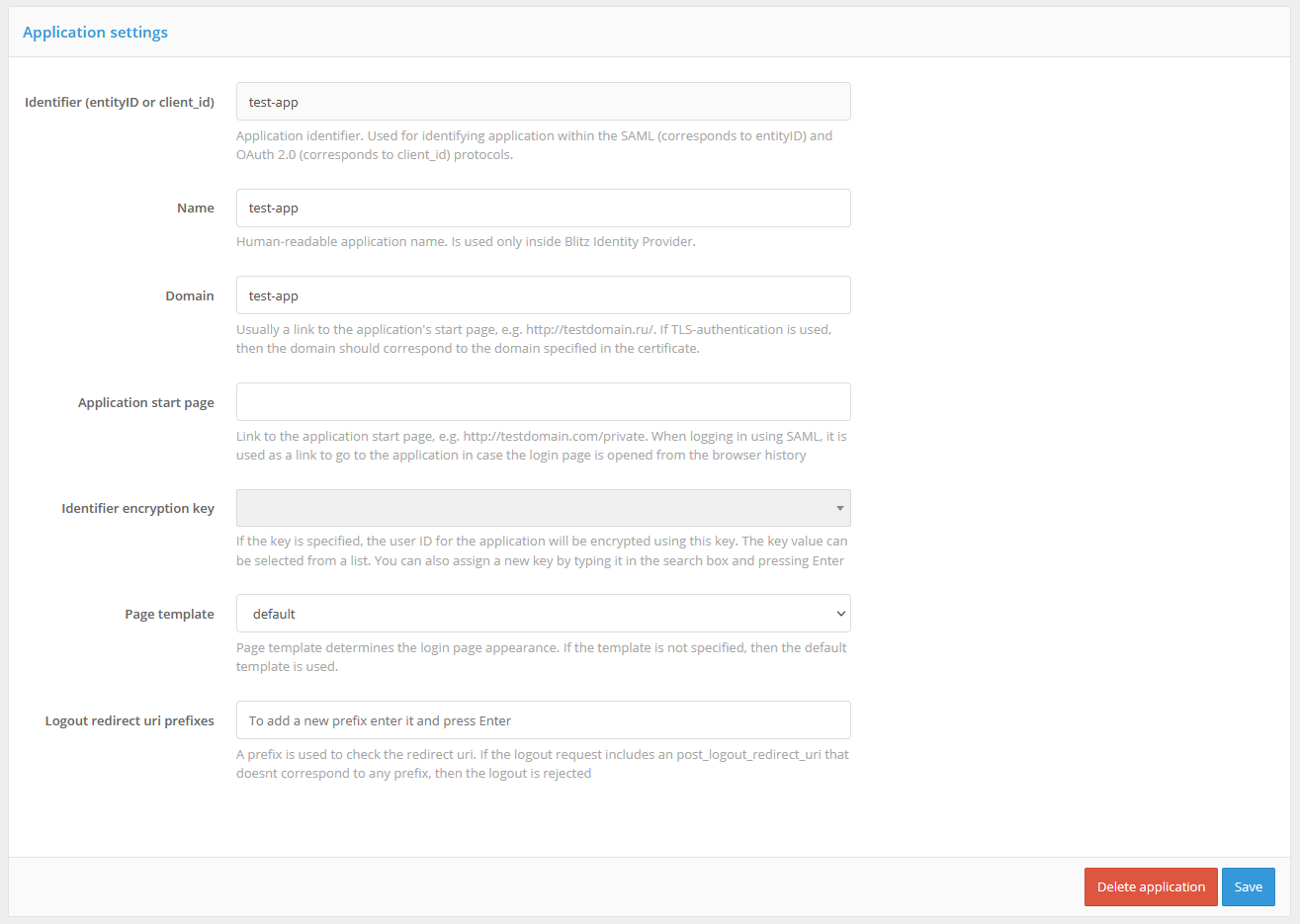
Step 2. Specify the application start page and select the login page template
In the “Application home page” field it is recommended to specify the application login link that initiates the identification and authentication request.
In the Page Template list, you must select which template should be used to display the login page when a user attempts to access this application. Instructions for creating a new template can be found here.
If necessary, you can specify the identifier encryption key (privacy domain). Creating a privacy domain ensures the uniqueness of the user identifier received by the application as a result of authentication, i.e. this identifier will be unique, but specific to this application. In other words, if a request for user data is initiated by an application from a different privacy domain, it will receive a different value of the user ID. Clicking on the field will display the previously configured encryption keys, with the option to set a new one. Applications that share a common encryption key will receive an identical User ID.
At this step, you can also set tags to further use them when customizing the application logic, e.g. to analyze them in a login procedure.
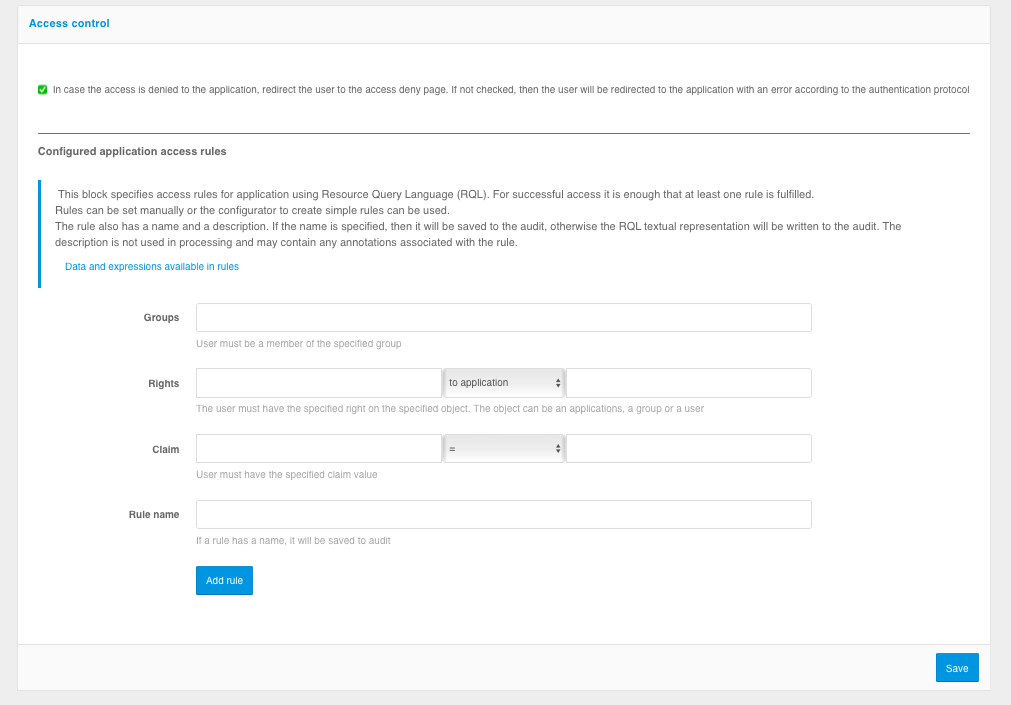
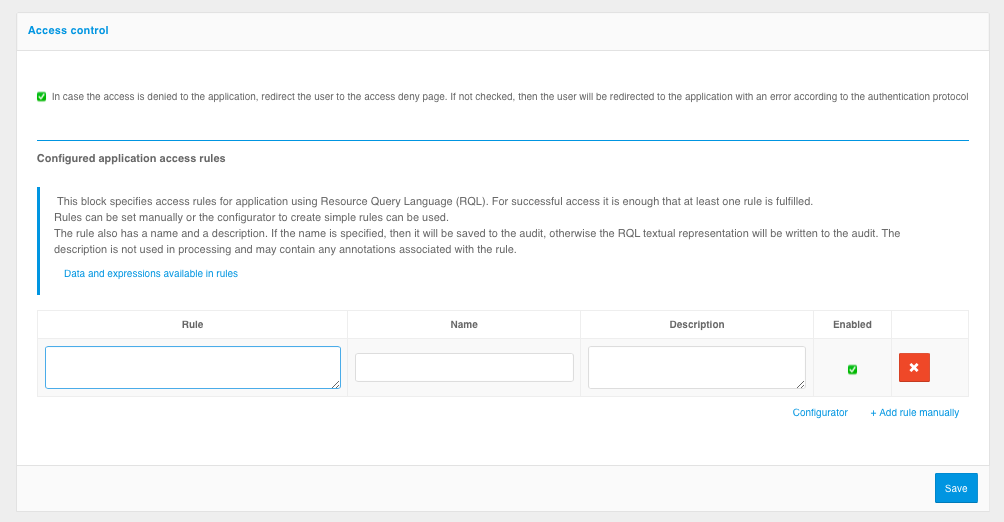
Step 3. Configure application access rules
You can configure the rules that Blitz Identity Provider uses to decide whether or not to allow a user into an application.
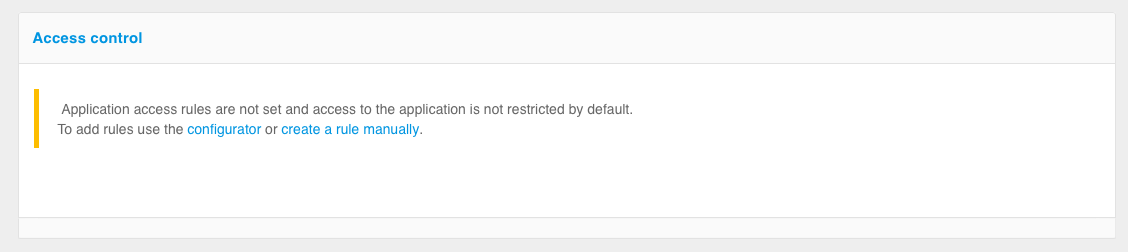
Access control rules can be added using the configurator or manually using RQL expressions (see figures below). In the rules it is possible to check that the user is included in the required user group (setting Groups in the configurator or rule contains(grps,GRP1,GRP2,...)), has the required access right (setting Authority in the configurator or rule contains(rights.its.SYSTEM,RIGHT_1,RIGHT2,...)) or has the specified attribute value (setting Approval in the configurator or expression with attribute).
Step 4. Connectivity protocols settings
You must configure one or more protocols for connecting the application to Blitz Identity Provider.
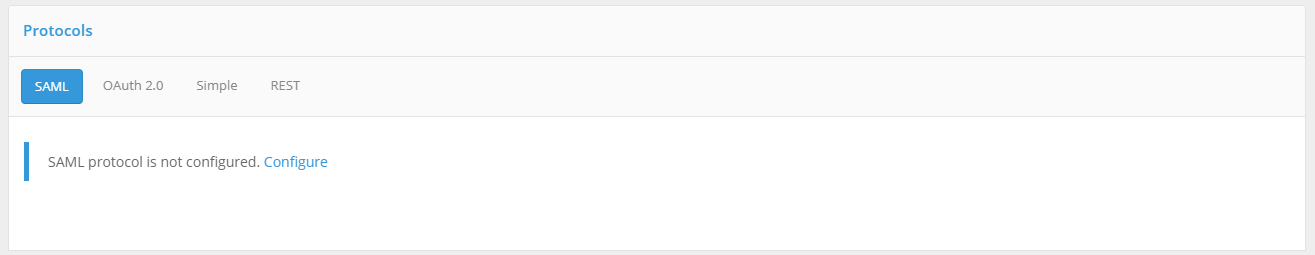
The following connectivity protocols are supported:
SAML - for connecting applications via SAML 1.0, 1.1, 2.0, and WS-Federation for user identification and authentication.
OAuth 2.0 - for connecting applications via OAuth 2.0, OpenID Connect 1.0 (OIDC) for user identification and authentication. Dynamic client registration can be configured within this protocol.
Simple - for connecting web applications to perform identification and authentication by substituting a login and password from a proxy server into the application, if the application does not support SAML/OIDC connectivity.
REST – connecting applications that use the REST services of Blitz Identity Provider for account registration/ modification, user authentication device management.
RADIUS – to connect to network services using the RADIUS protocol.
If an organization plans to develop or modify its own applications to connect them to Blitz Identity Provider, developers should review Integration Guide.
If an organization plans to connect applications that have native support for SAML 1.0, SAML 1.1, SAML 2.0, WS-Federation, or OIDC (OpenID Connect 1.0, OAuth 2.0) connectivity to Blitz Identity Provider, the following subsections describe the general settings on the Blitz Identity Provider side of connecting an arbitrary SAML/OIDC-enabled application.