Time-based one-time password log-in confirmation (TOTP)#
Any devices and programs compatible with the RFC6238 “TOTP: Time-Based One-Time Password Algorithm” standard may be used to verify the second factor of authentication using the Time-Based One-Time Password (TOTP) authentication method. These may include:
hardware keyfobs (one-time password generators) based on time;
mobile apps.
Note
The most well-known applications for generating TOTP codes are Google Authenticator, Twilio Authy, FreeOTP Authenticator, Microsoft Authenticator.
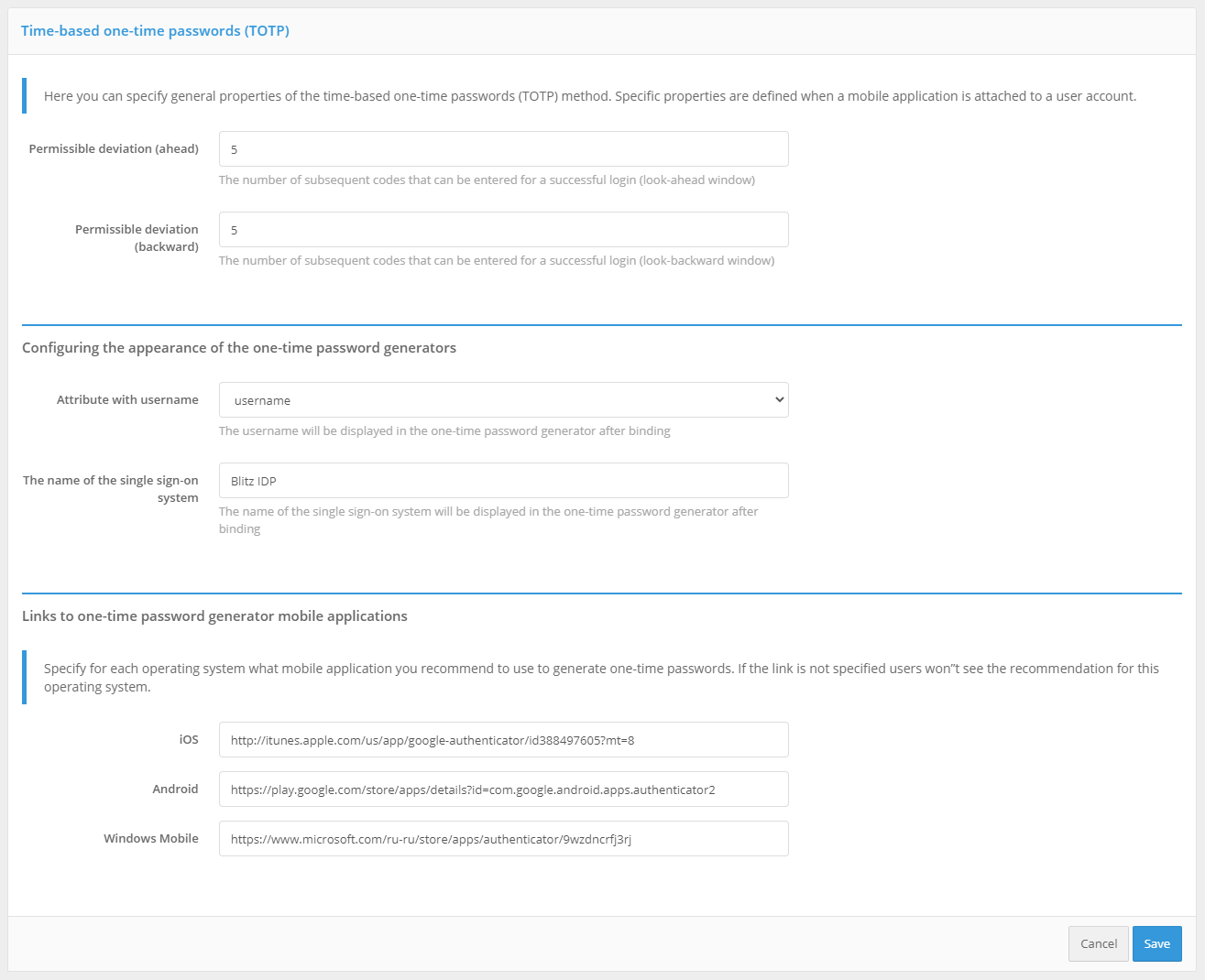
In the settings for the authentication method “Time-based One-Time Password (TOTP)”, you must specify:
Allowable code validation deviation (number of previous / next codes). By default, both values are
1: a user can enter both the current validation code and the next or previous one (generated in neighboring time intervals) when logging in. Such a need may arise, for example, to compensate for possible minor unsynchronization of server time and time on TOTP-devices of users.Customize the display of one-time password generators, which includes “Attribute with user name” and “Name of the single sign-on system”. These settings will be displayed in the mobile app after the user account is linked.
Links to one-time password generator applications. Links to applications that are recommended to be used by users should be specified. These links will be offered to the user in the web application User profile.