Simple#
You can use this method to connect an application to Blitz Identity Provider under the following conditions:
An application cannot be connected to Blitz Identity Provider using standard SAML or OIDC protocols.
The application is a web application deployed in its own infrastructure (On-Premise). User access to applications can be organized through a reverse proxy server.
To connect an application to Blitz Identity Provider using the Simple protocol, you must:
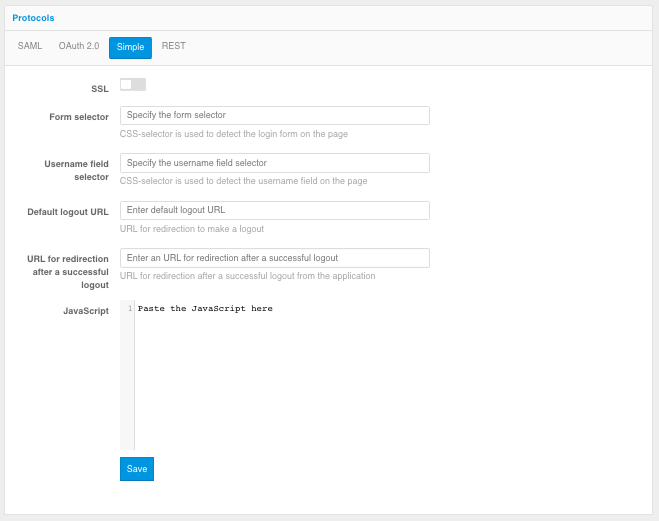
In the application settings in the Admin Console, select the Simple protocol and set its settings:
SSL - a setting that specifies whether the proxy calls the application connected by Simple via HTTP or HTTPS. It is recommended to use an existing web server of the application as a proxy server protecting the application, in which case the connection between the proxy server and the application will be made without TLS/SSL encryption.
Form selector - specifies a CSS selector to define the position of the login form on the plug-in application page.
Login field selector - specifies a CSS selector to define the position of the login field on the login page of the plug-in application.
Default Logout URL (optional setting) - specifies which URL Blitz Identity Provider should call when it is necessary to initiate a logout in a Simple connected application in the case of a single logout in Blitz Identity Provider.
URL to go to after a successful logout - specifies which URL Blitz Identity Provider should call to redirect the user after a successful logout initiated by a Simple connected application.
JavaScript (optional setting) - JS code embedded in the login page of the Simple plug-in application, which allows to process the response received from the application with login results (check that the login was successful) and show an error about it in Blitz Identity Provider.
Example value:
var fm = document.querySelector('form[name=login]'); if (fm) { document.body.style.display = "none"; var err = document.getElementById('lost-password'); var errKey = err && err.innerHTML.indexOf('Incorrect password.') !== -1 ? 'incorrect_password' : 'unknown_error'; var kvp = document.location.search.substr(1).split('&'); kvp.push([encodeURI('error'),encodeURI(errKey)].join('=')); window.location.search = kvp.join('&'); } var aLogout = document.querySelector('#logout'); var href = aLogout ? aLogout.getAttribute("href") : null; if (href) { var lp = encodeURIComponent(href); var slp = document.createElement('script'); slp.setAttribute('src', 'https://idp.company.com/blitz/simple/slp?app=app_id&lp=' + lp); document.head.appendChild(slp); }An example of Simple protocol settings for an application is shown in the figure below.
Set the settings for proxying requests to the application on the web server.
The example of configuration file for nginx web-server:
map "" $idp_host { default <server hostname>:9000; } map "$http_Blitz_Idp" $idp_post_login { default "0"; "prepare-login" "1"; } map "$arg_passive" $activLogout { default "1"; "true" "0"; } upstream oc-web { server <application server hostname>:<application port>; } server { listen 80; server_name <application domain name>; # enforce https return 301 https://$server_name$request_uri; } server { listen 443 ssl; server_name <application domain name>; resolver 172.27.0.20 172.25.0.50 valid=300s; #resolver 8.8.8.8 valid=300s; #ssl_certificate /etc/nginx/cert/<path to SSL certificate>.pem; #ssl_certificate_key /etc/nginx/cert/<path to SSL certificate key>.pem; #ssl_certificate /etc/letsencrypt/live/app.company.com/fullchain.pem; # managed by Certbot #ssl_certificate_key /etc/letsencrypt/live/app.company.com/privkey.pem; # managed by Certbot access_log /var/log/nginx/oc-acs.log full; error_log /var/log/nginx/oc-err.log error; ### force timeouts if one of backend is died ## proxy_next_upstream error timeout invalid_header http_500 http_502 http_503 http_504; ### Set headers #### proxy_set_header Accept-Encoding ""; proxy_set_header Host $host; proxy_set_header X-Real-IP $remote_addr; proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $scheme; add_header Front-End-Https on; proxy_redirect off; proxy_set_header Cookie "$http_cookie;domain2auth=$host"; proxy_hide_header Content-Security-Policy; add_header Content-Security-Policy "default-src 'self' https://$idp_host; script-src 'self' https://$idp_host 'unsafe-eval'; img-src 'self' data: https://$idp_host; style-src 'self' 'unsafe-inline'; font-src 'self' data:; frame-src 'self'; connect-src 'self'"; location ~ <path to login page of the application>$ { #if ($http_referer ~* "/blitz/simple") { # set $idp_post_login "1"; #} if ($http_referer ~* "<main server domain name>") { set $idp_post_login "1"; } if ($idp_post_login = "1" ) { proxy_pass http://oc-web$request_uri; } if ($idp_post_login = "0" ) { proxy_pass http://$idp_host/blitz/simple/prepare$request_uri; break; } } location ~ /logout$ { if ($activLogout = "1") { return 302 https://<main server domain name>/blitz/simple/active_logout?app=$host; } proxy_pass http://oc-web$request_uri; } location / { proxy_pass http://oc-web; } }