System requirements#
Operating systems#
All Blitz Identity Provider installation options and the server types involved support the following operating systems:
CentOS 7/8 Rocky Linux 8/9 AlmaLinux 8/9 RHEL 7/8/9 Oracle Linux 8/9
Minimum requirements#
Deployments with medium availability and performance requirements are recommended for preparation of test environments and production loops. Follow the scheme below.
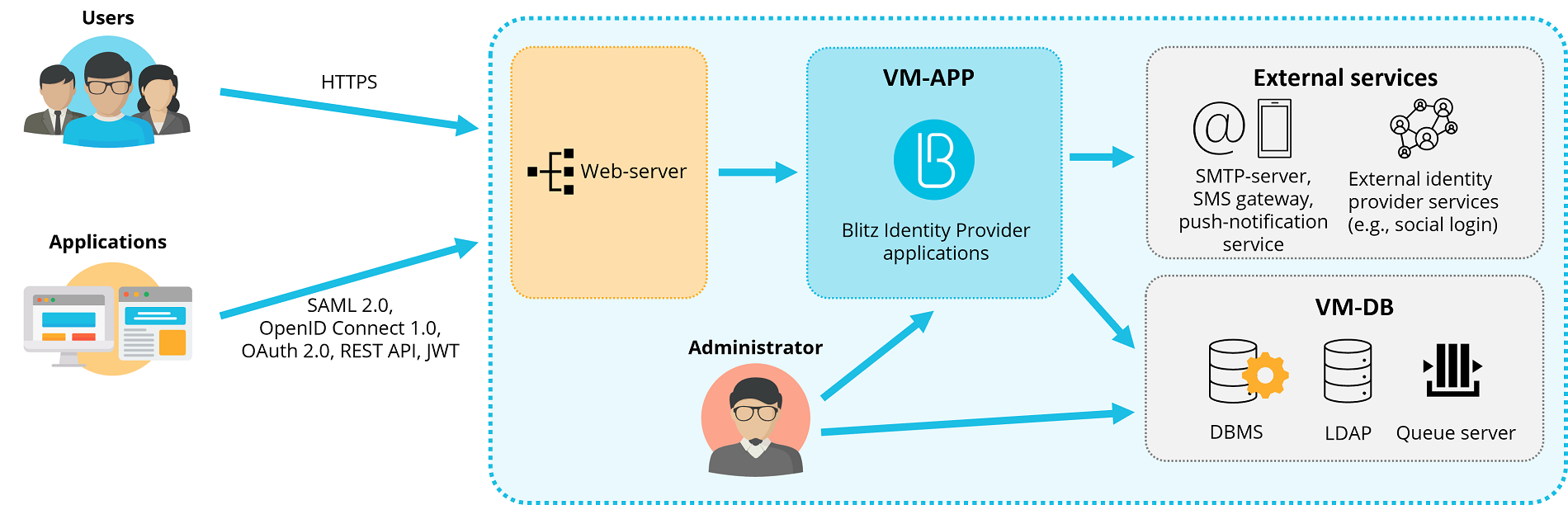
2 virtual machines (hereinafter - VMs) with the following characteristics and roles is a minimum requirement for the deployment.
Minimum sever requirements for deployment
Standalone deployment to 1 VM
Description |
Technical specifications |
Software |
|---|---|---|
VM for Applications and DBMS |
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
Blitz Identity Provider:
|
Standalone deployment to 2 VM
Description |
Technical specifications |
Software |
|---|---|---|
VM for Applications (VM APP) |
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
Blitz Identity Provider:
|
Database VM (VM DB) |
4 CPU cores, 8 GB RAM, 100 GB HDD |
PostgreSQL (9.6 or later) or Couchbase Server Community Edition (6.0 or later), 389 Directory Server or FreeIPA; RabbitMQ (optional) |
Cluster deployment to 2 VM
Description |
Q-ty |
Technical specifications |
Software |
|---|---|---|---|
VM for Applications and DBMS |
2 |
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
Blitz Identity Provider:
|
Required software versions:
OpenJDK 11 and Oracle JDK 11;
Memcached memory manager version 1.4.15 or higher.
Network connectivity requirements:
VM-APP shall be accessible via
80,443(HTTP/HTTPS) from user networks;VM-APP must have access:
to VM-DB via
8091,8092,8093,11209,11210,11211,4369,21100to21199,11214,11215,18091,18092(standard Couchbase Server ports),5432(standard PostgreSQL port),389,636(standard LDAP ports),5672(standard RabbitMQ port);to external identity provider services via
443port (if used):Links to the external identity provider services
Type
Reference
Social networks
https://appleid.apple.comhttps://accounts.google.comhttps://graph.facebook.com[1]to SMS gateway (if used);
to SMTP (if used);
to push notification service (if you use it);
to the Kafka service (when used to receive security reports).
For VM-APP, you need to create a public DNS name (for example, auth.domain.ru) and issue a TLS certificate for auth.domain.ru or *.domain.ru.
Recommended requirements for cluster#
Deployment in a cluster configuration is shown in the scheme below. Comply with the given requirements when building productive authentication loops with high availability and peak performance requirements.
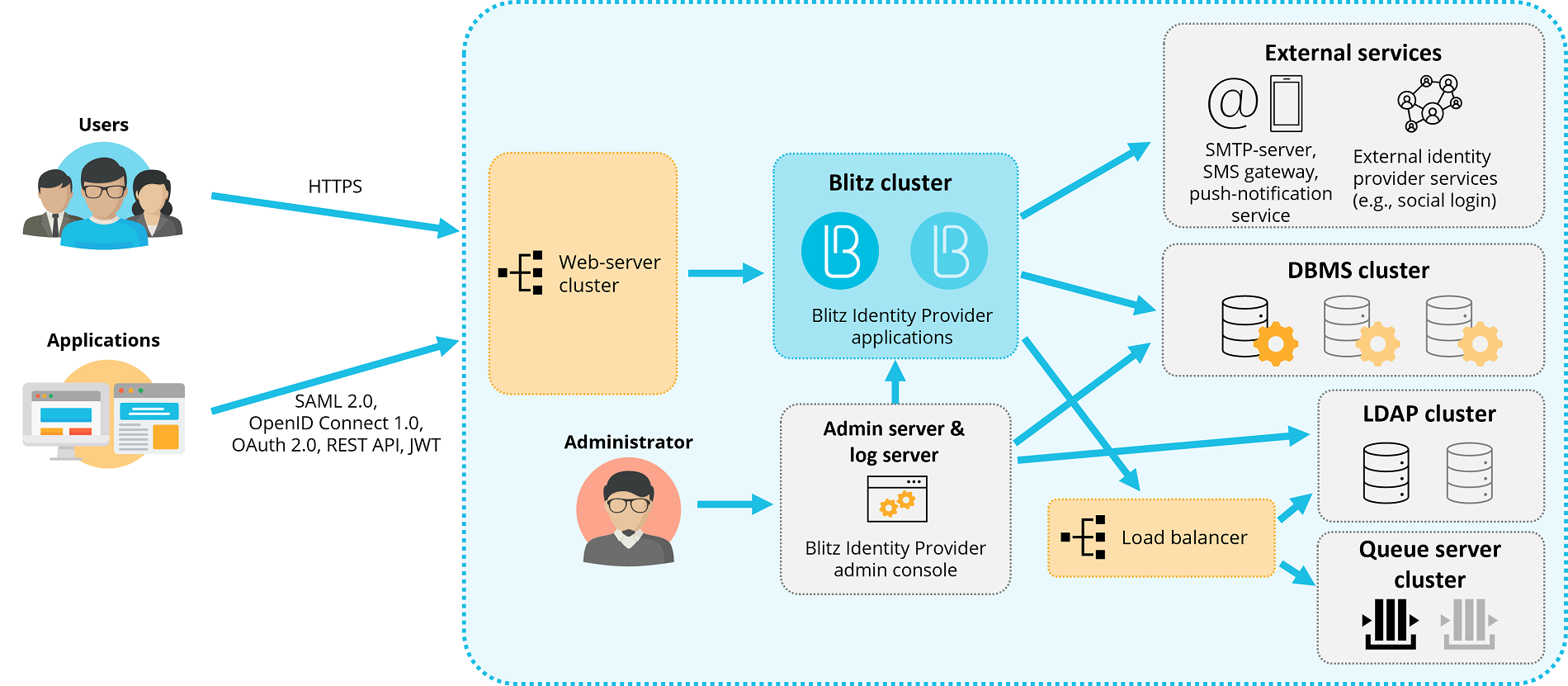
For deployment in a cluster configuration, it is recommended to use Virtual Machines (VMs) with the characteristics and functions listed in the table below.
Recommended server requirements for deployment in a cluster
Description |
Q-ty |
Technical specifications |
Software |
|---|---|---|---|
VM for web-servers (VM-WEB) |
1-2 |
4 CPU cores, 4 GB RAM, 50 GB HDD |
|
VM for Blitz Identity Provider applications (VM-APP) |
2 |
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
Blitz Identity Provider:
|
VM for console (VM-ADM) |
1 |
2 CPU cores, 4 GB RAM, 100 GB HDD |
|
VM for DBMS (VM-DB): |
2-3 |
For PostgreSQL: 4 CPU cores, 8 GB RAM, 100 GB HDD (data), 50 GB HDD (system). For Couchbase Server: 8 CPU cores, 16 GB RAM, 500 GB HDD (data), 100 GB SSD (indexes), 50 GB HDD (system). |
PostgreSQL software (9.6 or later) or Couchbase Server Community Edition (6.0 or later) |
VM ofr LDAP (VM-LDAP) |
2 |
4 CPU cores, 8 GB RAM, 100 GB HDD |
389 Directory Server |
VM for Queue server (VM-MQ) |
1-2 |
4 CPU cores, 8 GB RAM, 50 GB HDD (HDD) |
RabbitMQ version 3.7.9 |
VM for the Load balancer (VM-NLB) |
1-2 |
2 CPU cores, 4 GB RAM, 50 GB HDD |
|
Tip
VM-WEB:You can use an existing web server to load balance and remove TLS from incoming traffic.
VM-APP:Under heavy load, it is recommended to deploy Blitz Identity Provider services in its own clusters on separate servers.
VM-ADM:It is recommended to configure this server to collect logs from the other servers of the cluster.
VM-DB:For PostgreSQL, it is recommended to allocate one physical server for the main instance and one for standby. For Couchbase Server it is recommended minimum 3 VMs.
VM-LDAP:As a storage you can use an existing storage based on LDAP, Microsoft Active Directory, FreeIPA, or any other system for storing accounts and passwords (with the help of a relevant REST connector).
VM-MQ:Using a queue server is optional.
VM-NLB:Internal balancer is needed if LDAP and queue server are clustered.
Required software versions:
OpenJDK 11 or Oracle JDK 11;
Memcached memory manager version 1.4.15 or higher;
Network connectivity requirements:
VM-WEB shall be accessible via
80,443(HTTP/HTTPS) from user networks;VM-WEB must have access to VM-APP via
9000(blitz-idp),9002(blitz-registration),9003(blitz-recovery),9012(blitz-keeper),9013(blitz-panel) and to VM-ADM via9001(blitz-console);VM-APP must have access:
to other VM-APPs and VM-ADMs via
11211(memcached);to VM-DB via
8091,8092,8093,11209,11210,11211,4369,21100to21199,11214,11215,18091,18092(standard Couchbase Server ports) or5432(standard PostgreSQL port);to VM-LDAP (VM-NLB) via
389,636(standard LDAP ports);to VM-MQ (VM-NLB) via
5672(the standard RabbitMQ port);to external identity provider services via
443port (if used):Links to the external identity provider services
to the SMS gateway (if used);
to SMTP (if used);
to push notification service (if you use it);
to the Kafka service (when used to receive security reports).
VM-ADM must have access:
to VM-DB via
8091,8092,8093,11209,11210,11211,4369,21100to21199,11214,11215,18091,18092(standard Couchbase Server ports) or5432(standard PostgreSQL port);to VM-LDAP (VM_NLB) via
389,636(standard LDAP ports);to VM-APP via
22(ssh),514(rsyslog),873(rsync),11211(memcached);to VM-MQ (VM-NLB) via
5672(the standard RabbitMQ port);to the Kafka service (when using it to receive security reports)
from the VM-DB shall have access to other VM-DBs via
8091,8092,8093,11209,11210,11211,4369,21100-21199,11214,11215,18091,18092(Couchbase Server ports) or5432(PostgreSQL port);with VM-LDAP there must be access to other VM-LDAPs via
389,636(LDAP ports);from the VM-MQ must have access to other VM-MQs via
4369,35197,5672.
For VM-APP, you need to create a public DNS name (for example, auth.domain.ru) and issue a TLS certificate for auth.domain.ru or *.domain.ru.