Automatic user identification by session properties#
Blitz Identity Provider can perform automatic user identification and grant access based on pre-calculated session properties. Any session properties that can be defined by the Customer’s tools and provided in Blitz Identity Provider are supported.
Tip
A special case of using the method is the user logging in using a mobile phone number that is automatically determined by its IP address by the Customer-the mobile operator.
Attention
Automatic identification is possible only for the first factor.
To use this authentication method, follow the steps described below.
Step 1. Create the login procedure#
To use automatic identification, you must create a login procedure performed before passing the first authentication factor, which will request session properties from the Customer’s service. For example, in a special case, when logging in using an automatically determined phone number, the procedure should perform the following actions:
Determining the user’s IP address. If the IP address is in the specified range, the Customer’s mobile operator service is called to determine the mobile phone number.
After receiving the phone number, the procedure requests Blitz Identity Provider to log in using the automatic identification method.
Step 2. Add a method to blitz.conf#
In order for the automatic identification method to be displayed on the tab Authentication -> First factor, follow these steps:
Open the configuration file
/usr/share/identityblitz/blitz-config/blitz.conf.sudo vim /usr/share/identityblitz/blitz-config/blitz.conf
Add the method to the list of available methods of the first factor of the block
blitz.prod.local.idp.login.factorsby analogy with the example below. The methods of the first factor are specified in the first section of the block. The name of the method should consist of the prefixspropand an identifier: for example, the methodsprop_msisdnfrom the example has the identifiermsisdn.Note
You can add several methods.
"login" : { "factors" : [ [ { "enabled" : false, "method" : "sprop_msisdn" }, … ], [ … ] ], … }Restart the services.
sudo systemctl restart blitz-idp blitz-console
Step 3. Configure the method in the console#
The configuration of the method in the admin console is performed as follows:
In the admin console, go to Authentication -> First factor -> method settings Automatic identification.
Map the attribute stored in the Blitz Identity Provider data source to the session property received from the Customer’s service when performing the login procedure. After receiving the session property, Blitz Identity Provider will search for its value among the values of the specified attribute and, if successful, will allow logging in to the corresponding account. For example, mapping
phone_number=${p_msisdn}means that the session propertyp_msisdnwill be compared with the attributephone_numberin the data store.Tip
You can add several search conditions among the attributes that must be fulfilled simultaneously in order for the user to be identified, as well as enter an alternative rule.
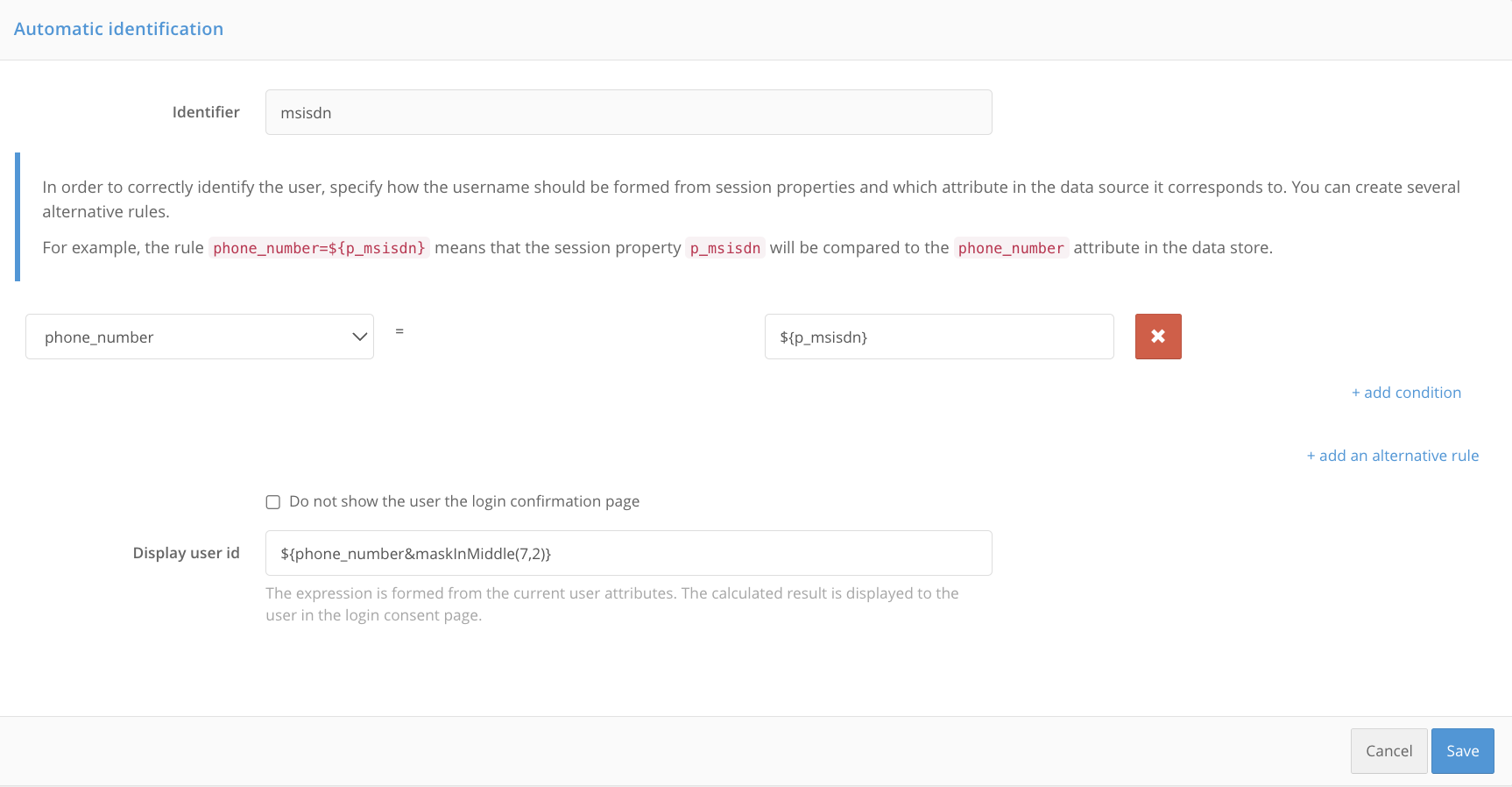
By default, after the user is automatically identified, their ID and a login confirmation request are displayed on their screen. Set a rule for generating a user ID from its attributes as a substitution string. This may be a disguised phone number, username, etc.
To deactivate the login confirmation, check the box Do not show the login confirmation screen to the user.
Click Save.
By default, users are searched for authentication in all active repositories. In the block Attribute Store Selection Rules you can set up rules that will search for a user in a specific store. You can set several alternative storage selection rules. This will allow you to authenticate some users using one storage, and others using another.
To create a rule, use the following components:
flag
not: indicates that the condition is inverted;the first column is the expression to be checked, for example, an attribute of an account, an application identifier, etc.;
the second column: the selection condition in the form of a regular expression, for example, the value of the user attribute, the value of the application identifier, etc.
For example, in order to authenticate all users whose phone number contains the code
980in the specified storage, create a rule as shown in the figure below.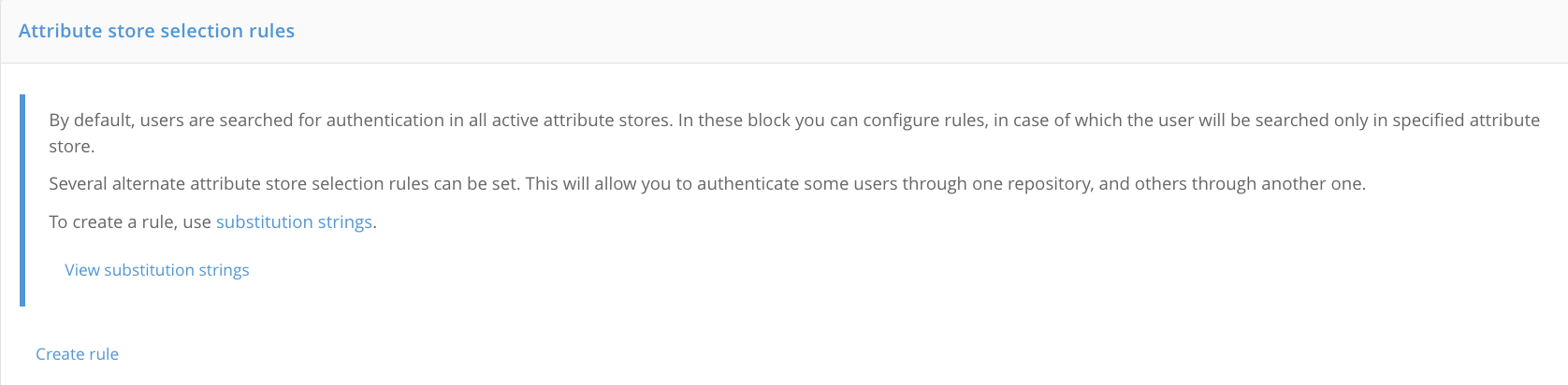
Click Save.
Step 4. Customization of texts#
If you use several methods of automatic identification, you should customize the interface texts for each of them, guided by algorithm.
You will need to include the method name or method identifier in the text string identifier. Method name is defined in the configuration file /usr/share/identityblitz/blitz-config/blitz.conf and consists of the prefix sprop_ and the method identifier: for example, the method sprop_msisdn has the identifier msisdn.
The following methods and strings are used for customization:
Login form
Customization using the method name <sprop_id>:
login.methods.sprop.head.title.<sprop_id>=Confirm log-in with phone number
login.methods.sprop.info.<sprop_id>=Your phone number<br><strong>{0}</strong>.
login.methods.sprop.btn.consent.<sprop_id>=Log in
login.methods.sprop.btn.refuse.<sprop_id>=Log in with another phone number
Displaying the method in the list of available methods during authentication
Customization using the method identifier <id>:
login.methods.switcher.title.sprop.<id>=Autologon with phone number
login.methods.switcher.label.sprop.<id>=Autologon with phone number
Displaying a method in the list of methods in the admin console
Customization using the method name <sprop_id>:
page.authn.<sprop_id>.title=Autologon with phone number
page.authn.<sprop_id>.info=To identify a user, we analyze a session property p_msisdn which is calculated and saved when the authentication flow starts.
Form of method configuration in the console
Customization using the method name <sprop_id>:
page.method.sprop.title.<sprop_id>=Autologon with phone number
page.method.sprop.info.<sprop_id>=<p>In order to correctly identify the user, specify how the username should be formed from session properties and which attribute in the data source it corresponds to. You can create several alternative rules. </p>For example, the rule <code>phone_number=$'{p_msisdn}'</code> means that the session property <code>p_msisdn</code> will be compared to the <code>phone_number</code> attribute in the data store.</p>
The result of executing the method on the Events tab of the admin console
Successful login: add the line
audit.method.<sprop_id>.Login failed: add the line
console.audit.type.auth_failed.<sprop_id>.
audit.method.<sprop_id>=Autologon with phone number
console.audit.type.auth_failed.sprop_msisdn=Error when logging in with phone number
Displaying an unsuccessful login event in the User profile
To display an unsuccessful login in the User profile, add the line profile.audit.type.auth_failed.<sprop_id>.
profile.audit.type.auth_failed.<sprop_id>=Error when logging in with phone number