Admin console settings#
The admin console is configured using the console.conf and credentials files. The following subsections describe the possible settings.
Logging in to admin console via SSO#
You can configure Blitz Identity Provider admin console to log in via the OIDC Identity Provider. The provider can be the current installation of Blitz Identity Provider, a custom installation of Blitz Identity Provider, or even an external software if it is compatible with OIDC.
The following admin console login modes are supported:
standard mode by the account login/password created in the section Administrators;
login via SSO;
the hybrid mode of logging in when the administrator can log in both by the login/password in the standard mode and using SSO.
If you are using the SSO mode, you don’t have to create administrator accounts in the section Administrators.
To configure the admin console login mode via SSO, do the following:
In the SSO identity provider settings, that will be used to log in to the admin console, register the admin console as an application. In the allowed return prefixes (
redirect_uri) specify the Blitz Identity Provider installation domain. As a result of the registration, you will get theclient_idandclient_secretparameters for the console;in the
console.confconfiguration file, create theloginsettings block with the following content:
{
"login" : {
"fp" : {
"authUri" : "https://idp-host.com/blitz/oauth/ae",
"clientId" : "blitz-console",
"clientSecret" : "client_secret_value",
"logoutUrl" : "https://idp host.com/blitz/login/logout?post_logout_redirect_uri=https://idp host.com/blitz/console",
"scopes" : [
"openid"
],
"subjectClaim" : "sub",
"roleClaim" : "roles",
"tokenUri" : "https://idp-host.com/blitz/oauth/te"
},
"mode" : "sso"
}
}
You must specify parameters:
In the
authUri``and ``tokenUriparameters, you must specify the addresses of the Authorization Endpoint and Token Endpoint handlers of the external identity provider.In the
clientIdandclientSecretparameters, specify the client_id and client_secret values, assigned to the application registered in the external identity provider application that corresponds to the admin console parameters.In the
logoutUrlparameter, specify the link to which the user should be redirected user when logging out of the admin console, so that a single logout via an external identity provider.In the
scopesparameter, prescribe the list of scopes which must be requested (at leastopenidscopes are needed).In
subjectClaimspecify the name of the attribute from the identity token (id_token) that is used as the account identifier. Using this identifier the administrator’s login will be performed inssologin mode.Specify in
roleClaimthe attribute name from the identification token (id_token), in which the role (string) or the role list (array of strings) of the administrator is passed. Using these identifiers the administrator’s login will be performed inssologin mode.In the
modeparameter, you must specify the required login page mode:sso- login only using an external identity provider (see the figure below);internal- login only using the login and password from the administration console settings. If the parameter is not specified, both options are available at the user’s choice. It is not required to create administrator accounts in the Administrators menu prior to logging in via SSO Logging in via SSO.
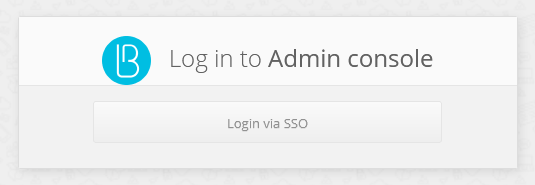
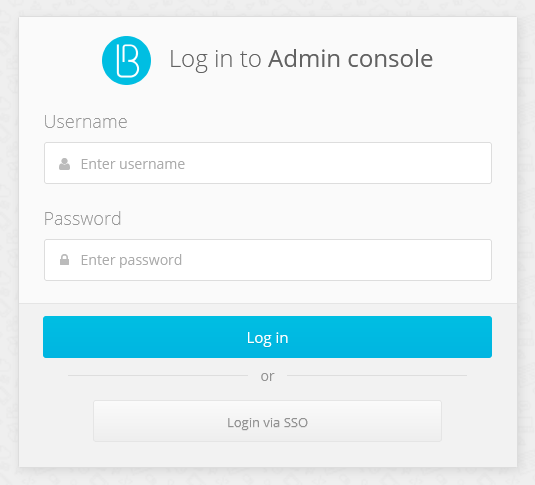
To avoid showing an intermediate login screen where the user clicks the Logging in via SSO button, you can invoke the admin console using a link of the following form: https://hostname:port/blitz/console?mode=SSO.
Session limit#
Security policy may require that a user or administrator cannot be logged in from multiple devices at the same time. To fulfill this security policy for administrator access to the admin console, the session block must be added to the console.conf configuration file:
"session" : {
"mode" : "exclusive",
"check-interval" : 10
}
With this setting, if an administrator login is detected with an account that has already logged in, the previous login will display the login page in the admin console for any action. The check-interval setting (specified in seconds) specifies the period of time in seconds how quickly the previous session will be logged out when a new session appears.
If the security policy also requires to prevent multiple sessions for normal users, this mode can be selectively enabled for certain users when logging in to certain applications. This can be done by configuring the login procedure.
Additionally, in the web application User profile it is necessary to enable the setting according to which an early log out from the web application will take place in case the user account is blocked or the policy prohibiting multiple user logins has been violated. In the blitz.conf configuration file, in the blitz.prod.local.idp.user-profile settings block, add the check-session-interval setting, which specifies the period of session activity check by the web application:
"user-profile" : {
"check-session-interval" : 10,
…
}
Roles and permissions for the console#
The standard administrator roles are described in the previous sections. In the credentials configuration file you can create additional administrator roles or correct access rights in existing roles. To do this, in the roles block, adjust the composition of access rights (privileges) corresponding to the role (name).
Example of configuration:
"roles" : [
{
"name" : "new-role",
"privileges" : ["w_app","w_system","w_ui","w_user","w_admin","r_audit"]
}
]
If new roles are created, text strings with role names must also be defined for them. Example of a text string for a new role new_role:
page.admins.role.new-role=new role name
The list of available access rights for filling the privileges setting is given in the table below.
Blitz Identity Provider admin console access rights
Access rights |
Available sections of the Admin console |
|---|---|
|
Applications |
|
Data sources, Authentication, Authentication flows, Identity providers, SAML, OAuth 2.0, Devices, Messages |
|
Self-services, Login page themes |
|
Administrators, Events |
|
User search, Group search, Access rights |
|
User search (read-only), Group search (read-only), Access rights (read-only) |
|
Events (read-only) |
Changing console admin password#
To change the console administrator password, do the following:
Open the file
/usr/share/identityblitz/blitz-config/credentials.Specify a new password in the
pswdHashparameter in plaintext without encryption. The system will encrypt it after changes are applied."users" : [ { "pswdHash" : "new$password", "roles" : [ "root" ], "username" : "admin" } ]
Restart the
blitz-consoleservice.sudo systemctl restart blitz-console